0×00000050蓝屏代码 蓝屏0x00000050怎么办
0×00000050蓝屏代码,Windows操作系统蓝屏是常见的问题之一,其中常见的错误代码之一就是0x00000050。这种蓝屏通常会伴随着错误信息的提示,例如PAGE_FAULT_IN_NONPAGED_AREA,这意味着Windows操作系统无法访问内存,造成程序运行错误或系统崩溃。这种错误可能由软件或硬件问题引起,因此需要进一步调查和排除故障。如果你遇到了0x00000050蓝屏代码的问题,不要慌张可以参考相关的解决方案,尝试修复Windows系统问题。
蓝屏0x00000050怎么办
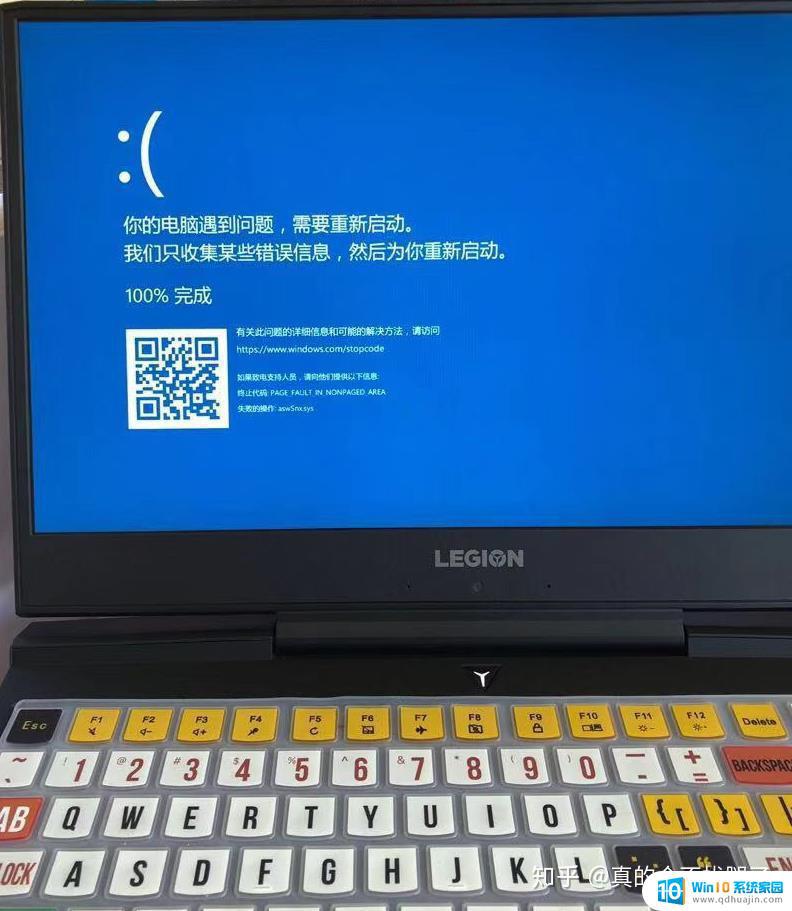
新机到手不到一周,一个午睡的功夫回来,电脑蓝屏了,风扇嗡嗡的响,长按电源键重启之后系统恢复正常了,总得找到蓝屏的原因吧。想了想电脑蓝屏之前应该是在试图卸载Avast Premium杀毒软件,电脑到手之后我卸载了自带的麦克菲。没有卸载联想电脑管家,安装了Avast Free,后来觉得Free功能单一就卸载了找了个密钥安装了Avast Premium,其实安装Avast的理由还是蛮简单的因为好卸载没弹窗,可能是安装时候提示安装包过期需要更新我没理愣是直接安装的原因,安装之后虽然也进行了漫长的更新但是程序总是卡死,于是决定卸载去官网下载安装包,事实证明安装包必须要来源合法否则真的会出现很多问题。大概就是这么个情况电脑蓝屏死机了,以这个为方向调查下原因。
【1】分析原因
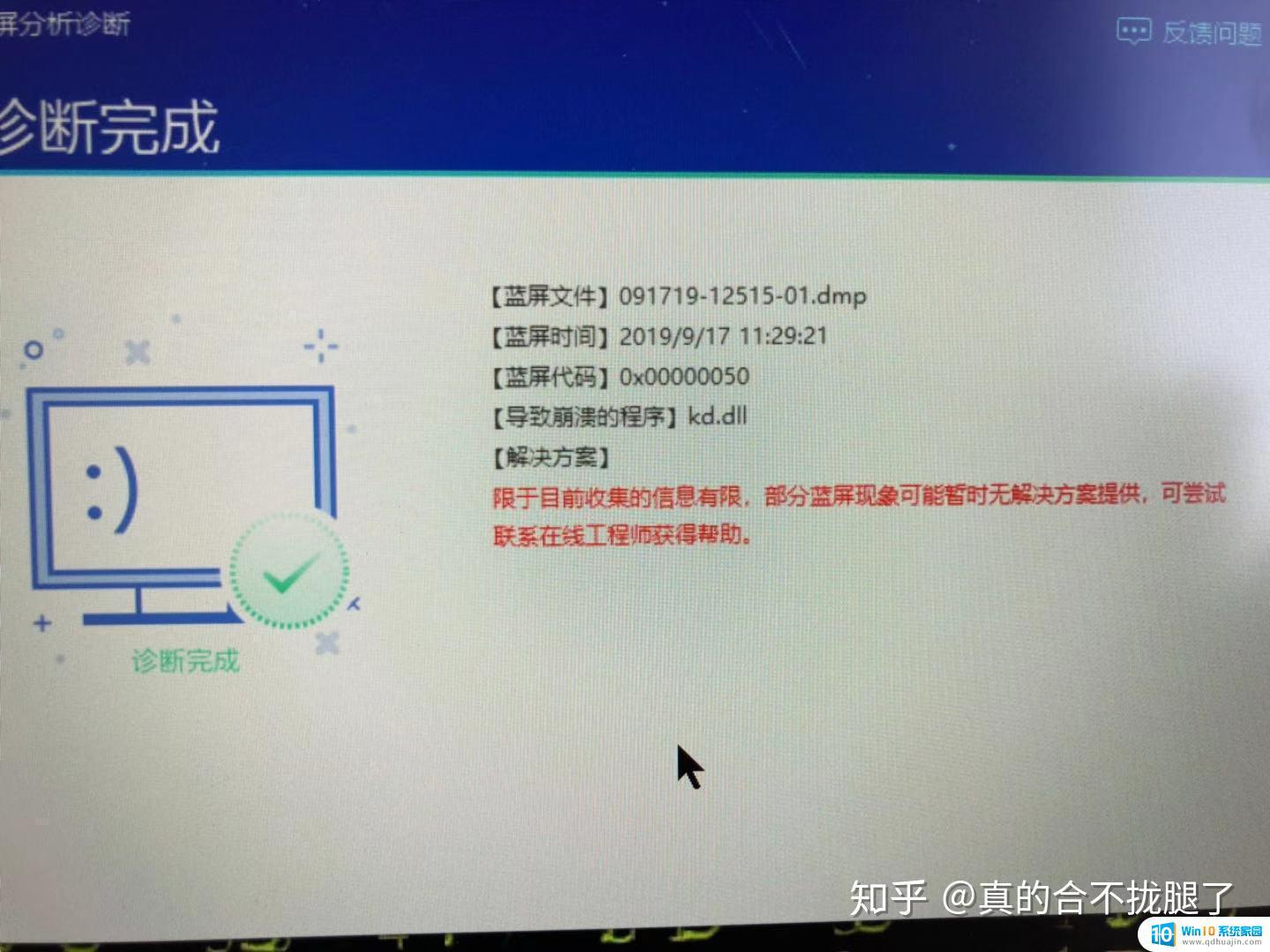
打开联想电脑管家->工具箱->蓝屏分析诊断

这一步主要是找到蓝屏错误代码->0x00000050
网上有很多蓝屏代码大全,字典参差不齐。这里直接粘贴一个官网的字典
0x00000050-------非故障区域的页面故障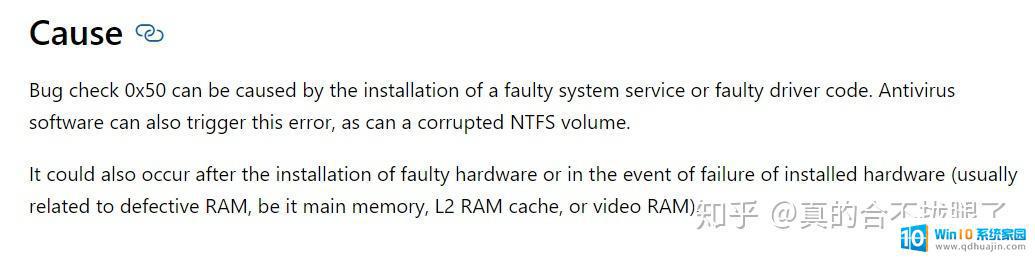 0x00000050错误代码官网解释原因
0x00000050错误代码官网解释原因0x00000050错误代码官网解释原因:
a.安装了错误的系统服务
b.安装了错误的硬件代码
c.安装了杀毒软件(杀毒软件的安装也会导致卷文件损坏)
d.硬件的错误安装
e.已安装硬件的错误事件(通常指内存故障)
这样看来本次蓝屏的原因果然是错误的安装杀毒软件了。
【2】解决方案
a.民间解决方案
其实重启可以解决99%的问题,事实上我的电脑重启后就什么问题都没有了,然而有些人会出现翻来覆去的蓝屏,或者重启蓝屏无限循环那就下一步
b.官网解决方案
 禁用杀毒软件或卸载。。。。
禁用杀毒软件或卸载。。。。其实官网上列出了很多方法我只把解决我的问题的方法列出来了,其它的等遇到了再更新吧
c.工程师解决方案
Typically, the referenced address is in freed memory or is simply invalid. This cannot be protected by a try - except handler -- it can only be protected by a probe or similar programming techniques.
Use the !analyze debug extension with the -v verbose option to display information about the bug check to work to determine the root cause.
dbgcmdCopy
2: kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* PAGE_FAULT_IN_NONPAGED_AREA (50) Invalid system memory was referenced. This cannot be protected by try-except. Typically the address is just plain bad or it is pointing at freed memory. Arguments: Arg1: ffffffff00000090, memory referenced. Arg2: 0000000000000000, value 0 = read operation, 1 = write operation. Arg3: fffff80240d322f9, If non-zero, the instruction address which referenced the bad memory address. Arg4: 000000000000000c, (reserved)
In this example Parameter 2 indicates that the bug check occurred when an area of memory was being read.
Look at all of the !analyze output to gain information about what was going on when the bug check occurred. Examine MODULE_NAME: and the FAULTING_MODULE: to see which code is involved in referencing the invalid system memory.
Look at the STACK TEXT for clues on what was running when the failure occurred. If multiple dump files are available, compare information to look for common code that is in the stack.
Use the .trap command provided in the !analyze output to set the context.
dbgcmdCopy
TRAP_FRAME: fffff98112e8b3d0 -- (.trap 0xfffff98112e8b3d0)
Use debugger commands such as use kb (Display Stack Backtrace) to investigate the faulting code.
Use the lm t n to list modules that are loaded in the memory.
Use the d, da, db, dc, dd, dD, df, dp, dq, du, dw (Display Memory) command to investigate the areas of memory referenced by parameter 1 and parameter 3.
dbgcmdCopy
2: kd> db ffffffff00000090 ffffffff`00000090 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000a0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000b0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000c0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000d0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000e0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`000000f0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? ffffffff`00000100 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
In this case doesn't look like there is data in this area of memory in parameter 1, which is the area of memory that was attempting to be read.
Use the !address command to look at parameter 3 which is the address of the the instruction which referenced the bad memory.
dbgcmdCopy
2: kd> !address fffff80240d322f9 Usage: Module Base Address: fffff802`40ca8000 End Address: fffff802`415fb000 Region Size: 00000000`00953000 VA Type: BootLoaded Module name: ntoskrnl.exe Module path: [\SystemRoot\system32\ntoskrnl.exe]
Use u, ub, uu (Unassemble)Dissasemble with parameter 3, to examine the which referenced the bad memory. For more information on X64 processor and assembly language see The x64 Processor.
dbgcmdCopy
2: kd> u fffff80240d322f9 nt!RtlSubtreePredecessor+0x9: fffff802`40d322f9 488b4810 mov rcx,qword ptr [rax+10h] fffff802`40d322fd eb07 jmp nt!RtlSubtreePredecessor+0x16 (fffff802`40d32306) fffff802`40d322ff 488bc1 mov rax,rcx fffff802`40d32302 488b4910 mov rcx,qword ptr [rcx+10h] fffff802`40d32306 4885c9 test rcx,rcx fffff802`40d32309 75f4 jne nt!RtlSubtreePredecessor+0xf (fffff802`40d322ff) fffff802`40d3230b c3 ret fffff802`40d3230c c3 ret
Use ub to dissassemble backwards from the a given address.
Use the r (Registers) command to examine what was being executed as the system bug checked.
dbgcmdCopy
2: kd> r Last set context: rax=ffffffff00000080 rbx=0000000000000000 rcx=ffffa68337cb7028 rdx=7a107838c48dfc00 rsi=0000000000000000 rdi=0000000000000000 rip=fffff80240d322f9 rsp=ffff840c96510958 rbp=ffffffffffffffff r8=ffffffffffffffff r9=0000000000000000 r10=7ffffffffffffffc r11=ffff840c96510a10 r12=0000000000000000 r13=0000000000000000 r14=0000000000000000 r15=0000000000000000 iopl=0 nv up ei ng nz na pe nc cs=0010 ss=0018 ds=0000 es=0000 fs=0000 gs=0000 efl=00010282 nt!RtlSubtreePredecessor+0x9: fffff802`40d322f9 488b4810 mov rcx,qword ptr [rax+10h] ds:ffffffff`00000090=????????????????
In this case fffff80240d322f9 is in the instruction pointer register, rip.
The !pte and !pool command may also be used to examine memory.
Use !memusage and to examine the general state of the system memory.
Driver Verifier
Driver Verifier is a tool that runs in real time to examine the behavior of drivers. For example, Driver Verifier checks the use of memory resources, such as memory pools. If it sees errors in the execution of driver code, it proactively creates an exception to allow that part of the driver code to be further scrutinized. The driver verifier manager is built into Windows and is available on all Windows PCs. To start the driver verifier manager, type Verifer at a command prompt. You can configure which drivers you would like to verify. The code that verifies drivers adds overhead as it runs, so try and verify the smallest number of drivers as possible. For more information, see Driver Verifier.
怎么说呢,看不懂所以懒得翻译,先粘贴上来等哪天有心情了再来研究。
d.其它解决方案
在我广泛查询之后,发现民间还有更改虚拟内存配置以解决蓝屏的方法。不知道究竟有没有用,关于虚拟内存实际需不需要配置,我觉得在我16G内存9代i7处理器面前实在是有点多余了以至于懒得研究,但是粘贴上来先,万一哪天需要研究呢
附几个链接
先这样未完待续
蓝屏代码0x00000050可能是由于软件或硬件驱动程序的问题引起的。要解决此问题,可以尝试运行系统更新、检查磁盘错误、更新或卸载驱动程序、检查内存问题等。如果以上方法均不能解决问题,建议联系专业技术人员以获得更多帮助。同时,定期进行系统维护和备份也是防止蓝屏的重要措施。
0×00000050蓝屏代码 蓝屏0x00000050怎么办相关教程
热门推荐
电脑教程推荐
win10系统推荐
- 1 萝卜家园ghost win10 64位家庭版镜像下载v2023.04
- 2 技术员联盟ghost win10 32位旗舰安装版下载v2023.04
- 3 深度技术ghost win10 64位官方免激活版下载v2023.04
- 4 番茄花园ghost win10 32位稳定安全版本下载v2023.04
- 5 戴尔笔记本ghost win10 64位原版精简版下载v2023.04
- 6 深度极速ghost win10 64位永久激活正式版下载v2023.04
- 7 惠普笔记本ghost win10 64位稳定家庭版下载v2023.04
- 8 电脑公司ghost win10 32位稳定原版下载v2023.04
- 9 番茄花园ghost win10 64位官方正式版下载v2023.04
- 10 风林火山ghost win10 64位免费专业版下载v2023.04